Access Control
Grant granular access to the schema (based on the user being logged-in, having some role or capability, or by IP), to manage who can access what data.

Click to watch tutorial video - 08:04
Define Access Control Lists to manage granular access to the API for your users.
Access Control Lists
This extension allows us to create Access Control Lists, to manage who can access the different elements (operations, fields and directives) from the GraphQL schema, using the following rules:
- Disable access
- Grant access only if the user is logged-in or out
- Grant access only if the user has some role
- Grant access only if the user has some capability
- Grant access only if the visitor comes from an allowed IP
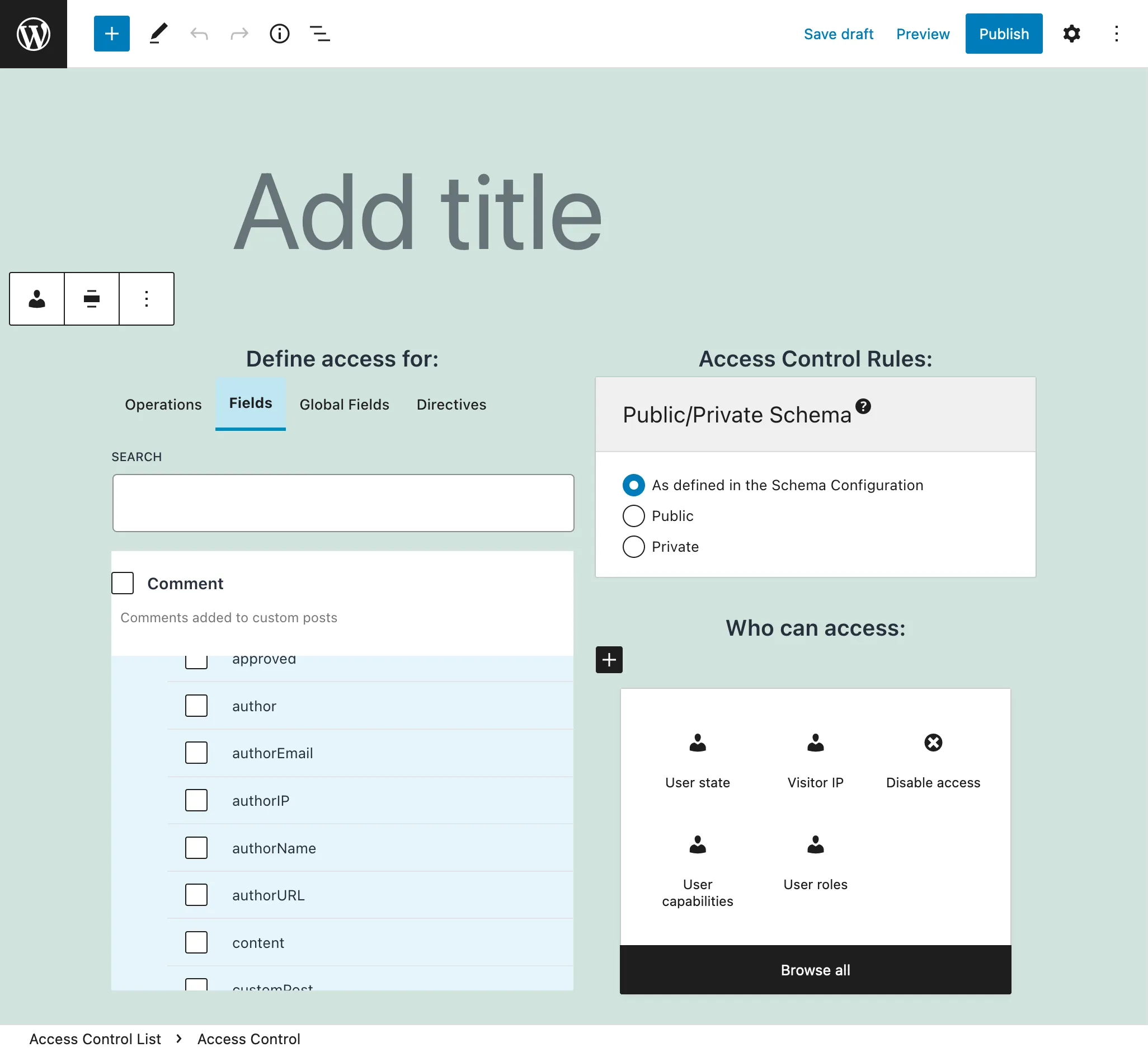
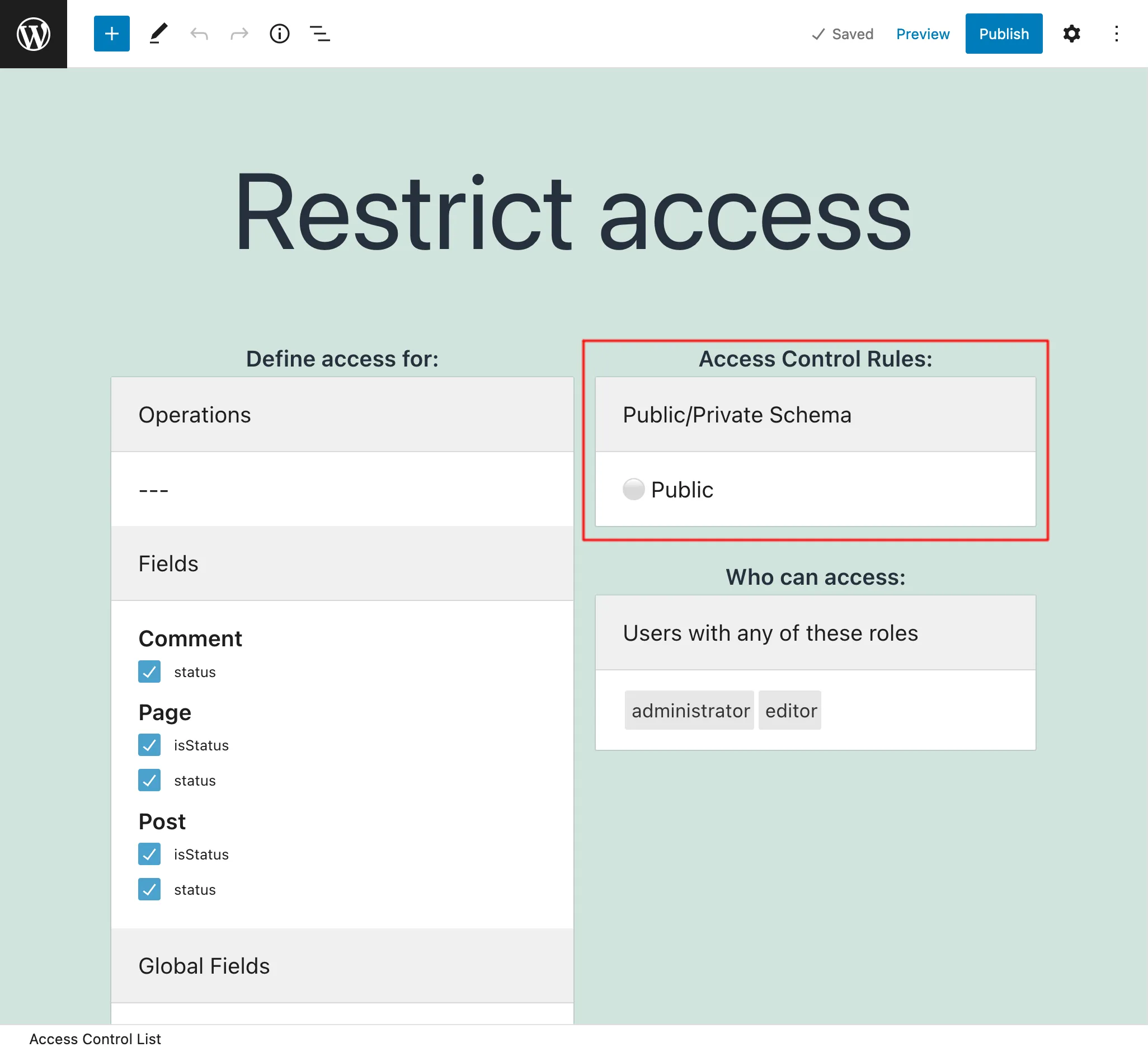
We indicate what rules must be satisfied to access what schema elements, from among operations, fields, global fields, and directives.
When executing a GraphQL query, if it contains any of the selected schema elements in the Access Control List, the chosen rules are evaluated.
If any rule is not satisfied, access to that operation, field or directive is denied.
Public/Private Schema Mode
When access to some a field or directive is denied through Access Control, there are 2 ways for the API to behave:
Public mode: The fields in the schema are exposed, and when the permission is not satisfied, the user gets an error message with a description of why the permission was rejected. This behavior makes the metadata from the schema always available.
Private mode: The schema is customized to every user, containing only the fields available to him or her, and so when attempting to access a forbidden field, the error message says that the field doesn't exist. This behavior exposes the metadata from the schema only to those users who can access it.
For instance, in the public mode, we may get this response:
{
"errors": [
{
"message": "You must have role 'author' to access field 'title' for type 'Post'",
"locations": [
{
"line": 86,
"column": 3
}
]
}
]
}While in the private mode we may get this response:
{
"errors": [
{
"message": "There is no field 'title' on type 'Post'",
"locations": [
{
"line": 86,
"column": 3
}
]
}
]
}


