Feature:
Multiple Levels of Security
Multiple Levels of Security
Several mechanisms to help protect your data:
👉🏽 Data that needs not be exposed can be removed from the GraphQL schema. For instance, if there's no need to expose user data, then disabling the Users module will remove the User type from the schema.
👉🏽 The single endpoint can be disabled, either by exposing pre-defined data via persisted queries.
👉🏽 All public endpoints can be disabled, forcing the user to first log-in to be able to access the GraphQL clients and endpoint.
👉🏽 Which settings (from table wp_options) and meta values (from tables wp_postmeta, wp_usermeta, wp_commentmeta and wp_taxonomymeta) can be queried must be explicitly defined in the configuration.
👉🏽 Some fields and input fields are exposed as “sensitive” data elements", as to provide access to private data, but have it disabled by default: public data (eg: posts) is accessible by default, private data from the user (myPosts) is available to the logged-in user, and input status in field posts(filter:) (to retrieve non-published posts) is accessible only if explicitly enabled.
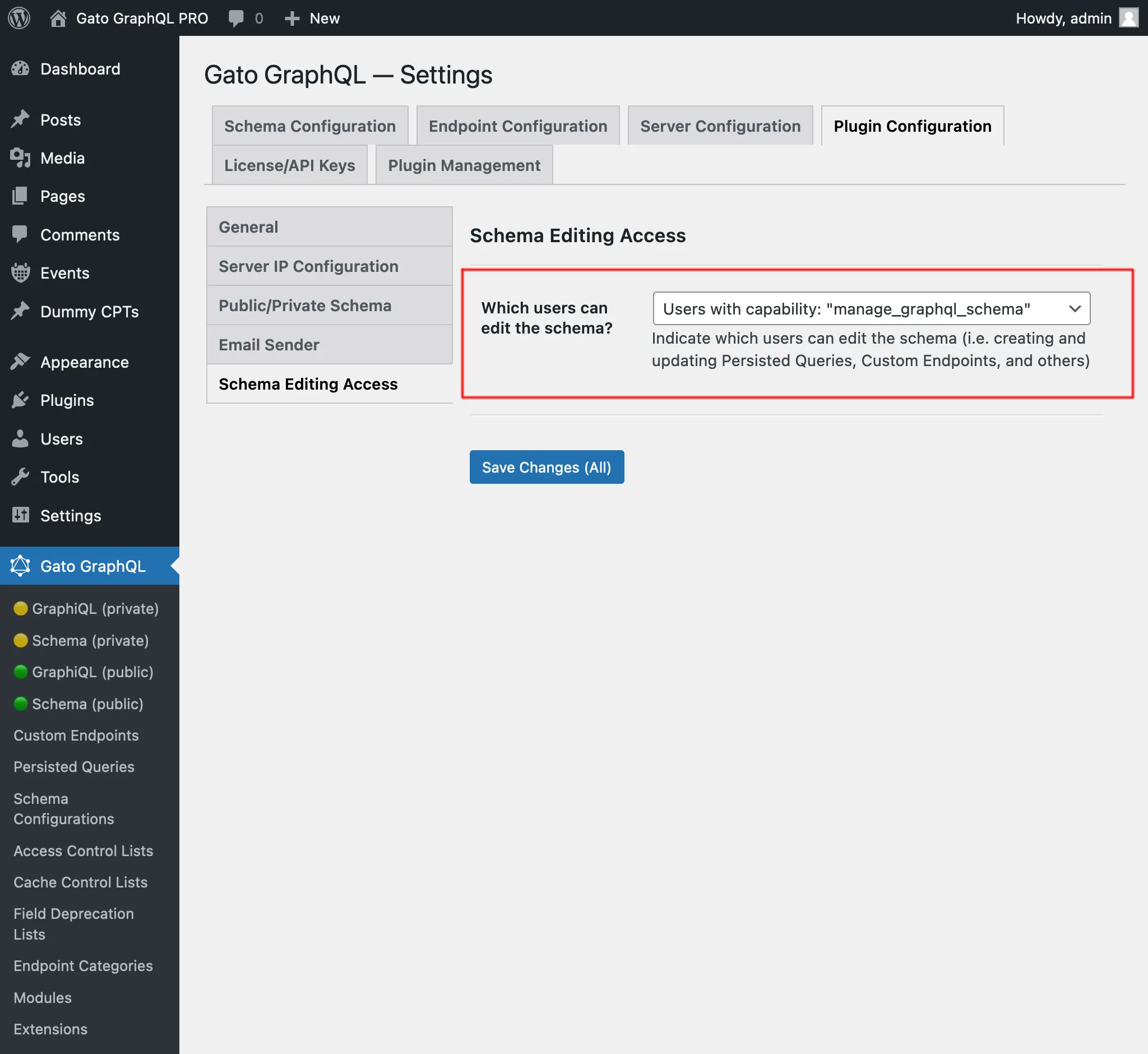
👉🏽 The admin can grant user-role access to editing the schema.
This image shows how we can grant access to editing the schema based on the user role: